Introduction
Don’t use passwords they said. It can be breached they said. Well, surprise, surprise, we didn’t pay much attention. Now, here we are, nervously checking our email IDs against the colossal 26 billion-record breach – the mother of all breaches!
Breach Unveiled: A Symphony of Chaos
So, there’s this massive breach, Mother of All Breaches (MOAB), a digital pandemonium that has exposed a whopping 26 billion records. It’s like a digital opera – records from MySpace to Adobe, starring Tencent, Weibo, Twitter, and LinkedIn. Your data just had its grand debut!
The Dramatic Unfolding
Picture this: MOAB is a blockbuster compilation of data breaches, meticulously curated. It’s like a Hollywood blockbuster, but your credentials are the star, and not in a good way. Your once-secure passwords are now part of a hacker’s treasure trove. Slow clap for the password drama.
Passwords – The Ultimate Blunder
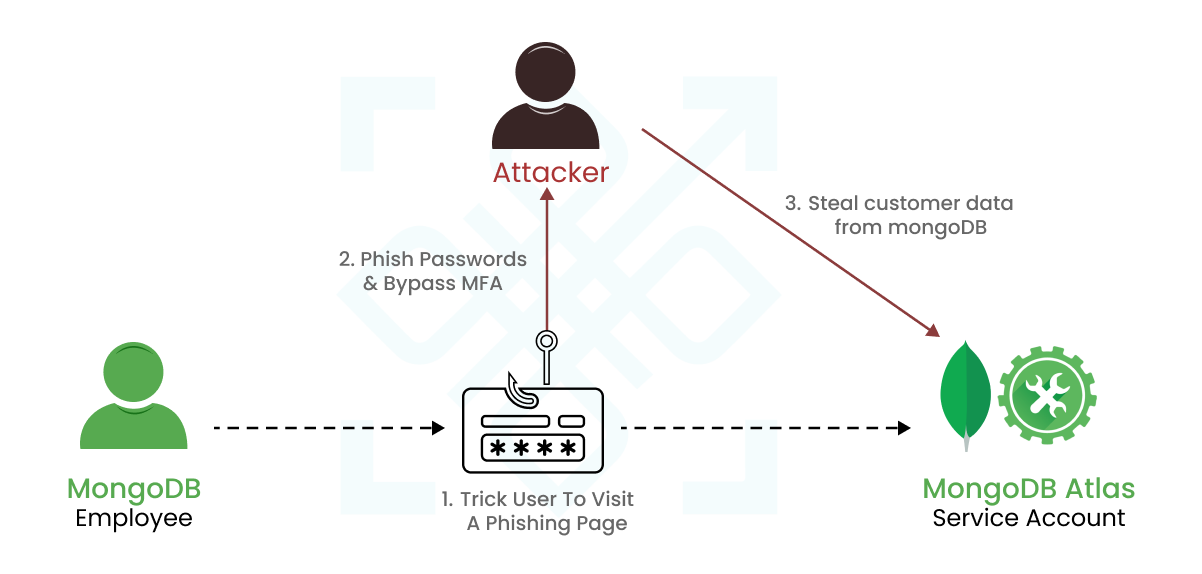
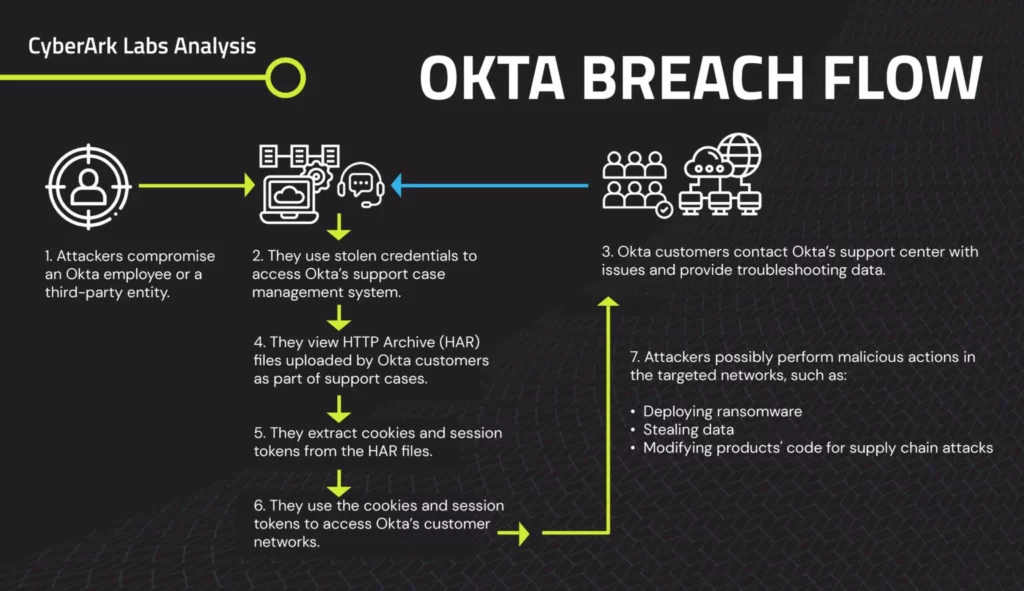
If Ellen DeGeneres hosted this show, she’d say, “You had one job – say no to passwords!” See the aftermath? Identity theft, phishing attacks, and a surge in password-stuffing shenanigans. All thanks to those outdated, reused, and easy-to-crack passwords.
Passwordless Paradise: Where Dreams Come True
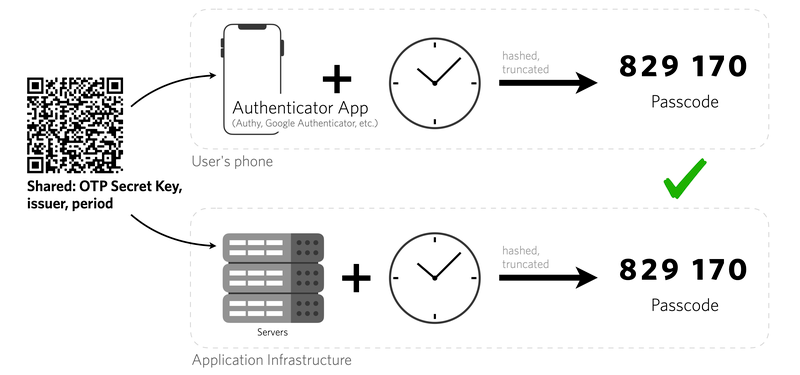
Now, imagine an alternate universe where you actually listened – where passwordless authentication is the superhero. No MOAB nightmares, just smooth, secure logins without the hassle of juggling countless passwords. A utopia, right?
Mitigation Party: Reclaim Your Digital Kingdom
Inspect Your Vulnerability: Employ tools such as “Have I Been Pwned” and data leak checker. data leak checker. Use “Privacy Hawk” to trace your data’s path and request removal from unwanted websites. Move swiftly: Purge your digital footprint by eliminating your data from irrelevant websites.
Conclusion: Lessons Learned (Hopefully)
In an ideal world, you’d have embraced passwordless authentication, and we’d all be sipping digital margaritas by now. But, alas, here we are – dealing with the aftermath. Take this as a digital wake-up call: passwords belong to the past, let’s march into a passwordless future.
A Final Plea: Break Free from Passwords
Passwords are so yesterday!! The revolution is calling – will you answer? Join the passwordless parade; your digital sanity will thank you later. Use PureId, Stay Safe.