Connect with Us!
Subscribe to receive new blog post from PureID in your mail box
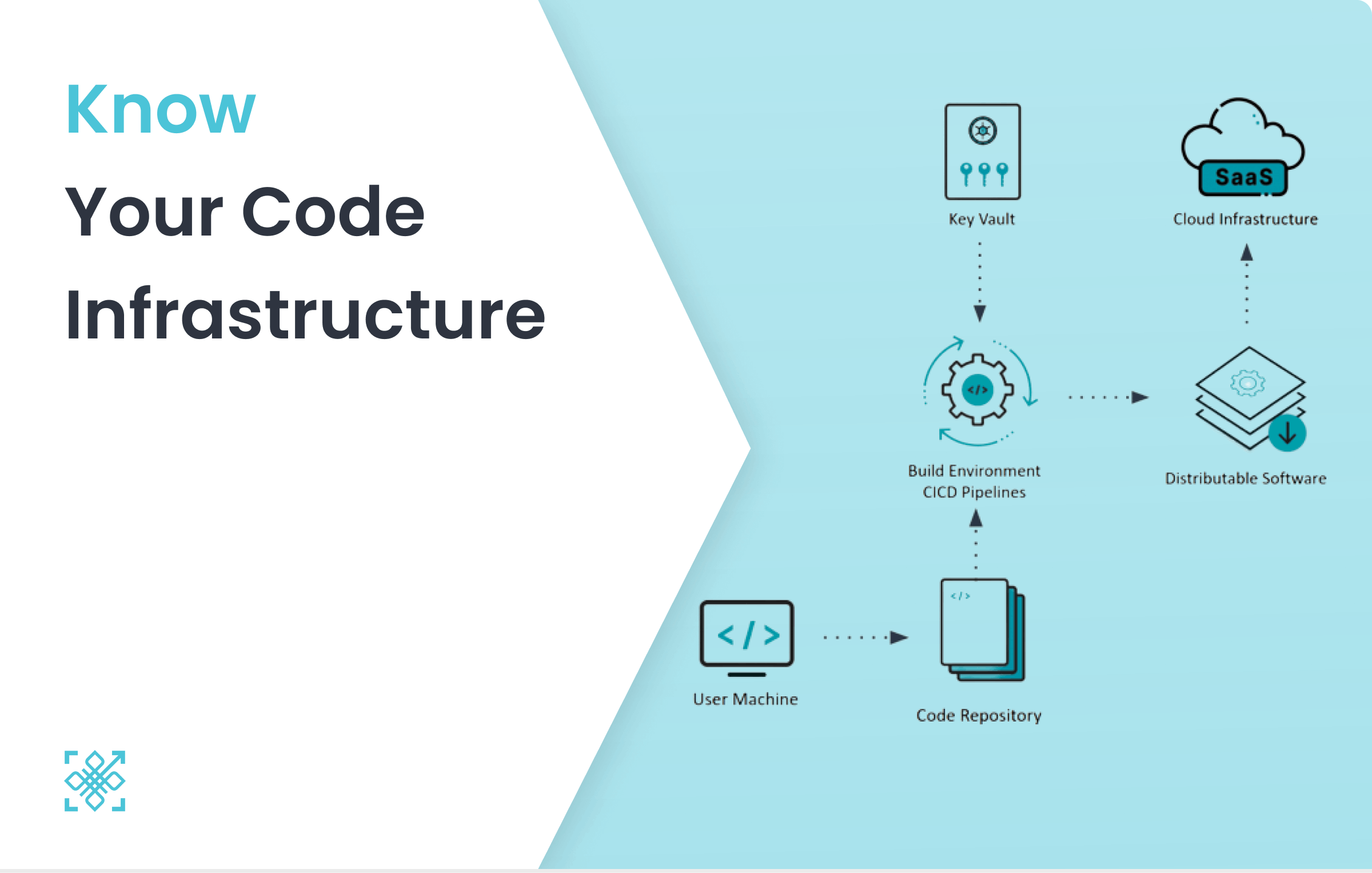
You must be familiar with IaC (Infrastructure as a Code). If not, Stackify has a very good primer on this topic. Code Infrastructure (CIx) simply involves all the tools and systems involved in the Software Development Life Cycle (SDLC process) of an organisation.
Recent supply chain attacks makes it evident, that adversaries world over are targeting the CIx (in other words SDLC tools) of the global software manufacturers. This write up will briefly explain various attacks on Code Infrastructure (CIx) components with the references of some recent supply-chain incidents.
Code Infrastructure (CIx) comprises of all the distributed applications / systems & artefacts that are involved with or result of each and every step involved in the Software Development Life Cycle (SDLC process). Here is how Code Infrastructure of a typical software engineering organisation looks like -
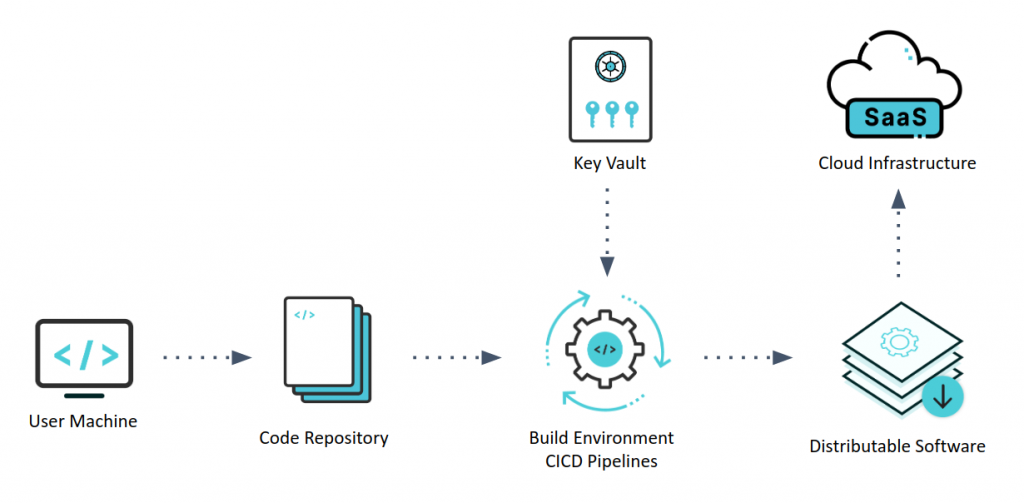
CIx presents a vast attack surface which is not often properly secured. This is evident In all the recent supply chain attacks that we have witnessed. We have seen all the attacks targeted to one or more CIx components.
| Incident | Target & Method | Reference |
|---|---|---|
| Target - Build Systems Method - Insertion of untrusted code | Solarwinds - SunBurst | |
| Target - Code Attestation System Method - Stolen Credentials | NVIDIA - Stolen Signing Keys | |
| Target - Deployed Vulnerable Code Method - Stolen Credential | Kaseya CVE-2021-30116 | |
| Target - Code Management System Method - Stolen Credentials | NPM Supply-Chain Attack | |
| Target - Deployment Platforms Method - Stolen Credentials | Mime Cast - Attacks in Cloud |
It becomes very crucial for enterprises to pay attention to their CIx and secure the attack vercorts applicable for each of these components.
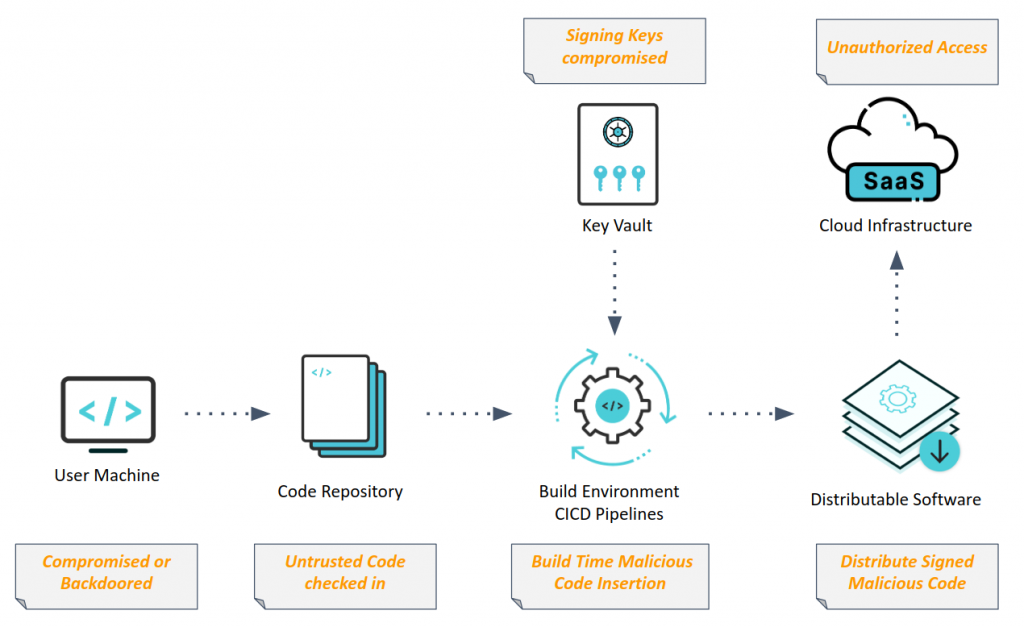
The majority of attacks we have seen are due to exploitation of the Identity & Trust framework. In all the cases Identity was managed by conventional passwords and MFA/2FA. The trust breach happened due to leaked signing keys (private keys), access to which was not properly secured.
In the case of Solarwinds we can also see that the build systems built and distributed untrusted code. This happened due to the absence of a Trust framework which can automatically verify that the code being built is a work of a verified/trusted engineer and not a malicious actor.
The careful study of all supply chain attacks in recent times clearly shows the industry needs to move to a better Identity & Trust framework. We need better Identity management to control access to our CIx resources and robust Trust Framework to verify sanctity of the deliverables at each and every level in software engineering, both pre & post built.
PureAUTH provides a breach resilient Identity & Trust Platform using its innovative Zero User Data Initiative (0UDI).
To learn more, how PureAUTH is used by various organisations to secure access to their CIx resources and Build Trust in all relevant user actions, schedule a demo with us.
Subscribe to receive new blog post from PureID in your mail box