Connect with Us!
Subscribe to receive new blog post from PureID in your mail box

Microsoft Entra ID, previously known as Azure Active Directory (Azure AD), provides a unified identity management solution for both on-premises and cloud-based applications. One key feature of Entra ID Pass-Through Authentication (PTA), which allows users to sign in using the same password for both environments. This setup aims to enhance user experience and reduce IT support costs.
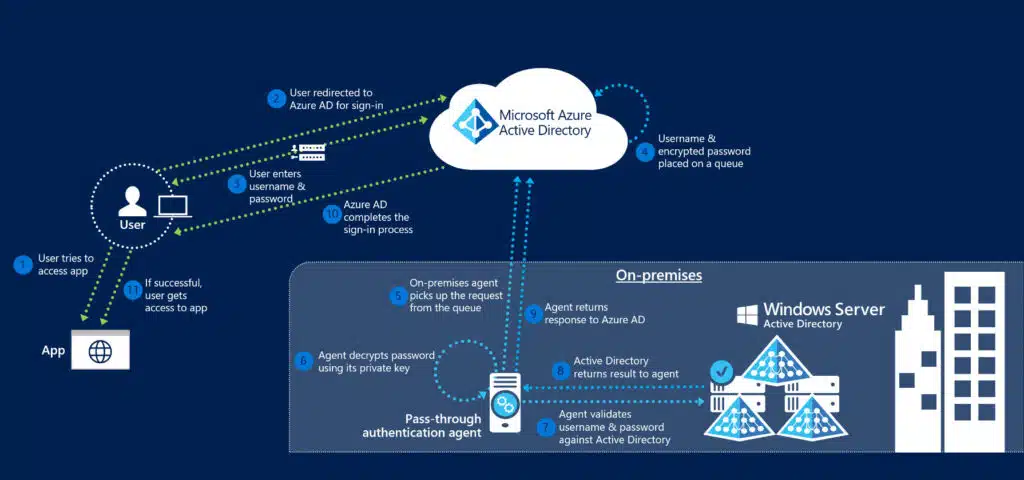
In PTA, the system validates users’ passwords against the on-premises Active Directory (AD) instead of storing them in the cloud. When a user tries to log in, Azure AD redirects them, and they enter their credentials. The system encrypts these credentials and sends them to a queue. An on-premises PTA agent retrieves the credentials from the queue, decrypts them, and checks them against the on-prem AD. The agent then sends the result back to Azure AD to complete the login process.
A recent vulnerability has exposed critical flaws in Microsoft Entra ID’s PTA mechanism. Researchers have discovered that attackers with local administrative privileges on a PTA agent can bypass authentication controls. This flaw allows attackers to impersonate any synchronised user without knowing their actual password.
This vulnerability effectively turns the PTA agent into a “Double Agent,” granting unauthorised access to any user account, including those with elevated privileges. If exploited, attackers could potentially gain full network privileges across the enterprise, posing significant risks.
To mitigate these risks, Microsoft suggested treating the Entra Connect server as a Tier 0 component, along with hardening the Microsoft Entra Connect server as a Control Plane asset.
Additionally, organizations should implement several key security measures:
Time and again we have seen Microsoft and other traditional IAM solution providers rely on passwords & fail to provide secure authentication across cloud and on premise environments.
For more secure & reliable authentication, enterprises can depend on PureAUTH IAM firewall which protects enterprises from all credential based attacks and such 0 day vulnerabilities.
The Microsoft Entra ID vulnerability highlights the importance of securing authentication mechanisms and understanding potential weaknesses in identity management systems. With the constantly changing best practices implementing secure authentication is difficult. Organisations must constantly work to protect themselves from such threats.
For more details, refer to the Cymulate blog post and Microsoft’s official security advisories.
Subscribe to receive new blog post from PureID in your mail box