Introduction
Active Directory Certificate Services (AD CS) may seem like a helpful gatekeeper for managing digital certificates and encryption, but if it’s not configured just right, it can leave the door wide open for hackers. AD CS is often overlooked when it comes to security, making it a perfect treasure trove for attackers. And once they’re in, they can sneak around undetected, establishing long-term persistence in your network like they’re on an extended vacation.

In this blog, we’ll break down how hackers exploit AD CS, dive into some clever tactics from recent findings, and most importantly, explain what you can do to keep them out.
Hackers in the Shadows: How AD CS Is Exploited
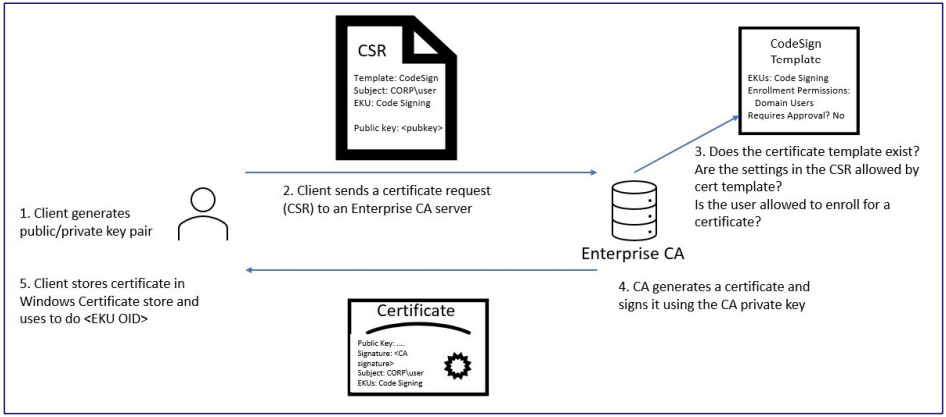
AD CS is Microsoft’s Public Key Infrastructure (PKI) solution for issuing and managing digital certificates in Active Directory environments. When configured correctly, it helps secure network communications. But if misconfigured, AD CS can quickly become a hacker’s best friend, enabling them to access networks, steal credentials, and stay hidden for the long haul.
Key Attack Vectors
- Stealing Certificates: Imitation is the Best (Criminal) Strategy
Hackers can grab user or machine certificates, along with private keys, and use them to impersonate legitimate users or machines. This is like copying someone’s ID, if the certificate remains valid, they can continue authenticating, even after passwords change. - Requesting Fake Certificates: Elevation Without the Effort
Imagine asking for a regular office key but getting access to the CEO’s office instead. Similarly, if there are any misconfigured certificate templates, low-privileged users can request certificates that grant admin-like privileges. - Misconfigured Certificate Templates: Unintentional Free Pass
Certificate templates can be dangerous when they allow attackers to specify Subject Alternative Names (SANs). This essentially hands over the keys to high-level users’ certificates—like getting access to a domain admin’s credentials. Templates that aren’t secured give attackers serious access. - CA Private Key Theft: A Permanent Invitation
If an attacker can get their hands on a Certificate Authority (CA) private key, they can generate certificates for any user in the domain. This grants them persistent access that’s nearly impossible to revoke. - Become a Shadow CA
If an attacker can get a certificate signing request (CSR) signed by CA, which has constraint isCA is set to True, and allowed its use for signing other certificates, then the issue\d certificate makes the attacker a Parallel CA, which can independently generate any arbitrary certificates which will be considered as valid.
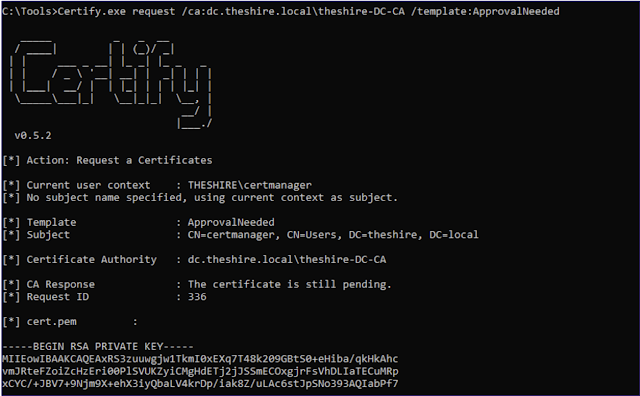
Tools of the Trade: Certify and ForgeCert
Hackers aren’t going in blind—they’ve got tools that make exploiting AD CS a breeze. The whitepaper by Will Schroeder and Lee Christensen highlights two key tools:
- Certify: This tool scans for AD CS misconfigurations and assists attackers in requesting malicious certificates. It functions like a vulnerability scanner specifically designed for certificates.
- ForgeCert: Attackers use this tool to create fake certificates with a stolen CA private key. By forging these certificates, they gain permanent access to your network, making detection much more challenging.
Mitigation: Fortify Your AD CS Before It’s Too Late
So, how can companies stop attackers from abusing AD CS? It’s all about treating your certificates like they’re gold and your CAs like they’re Fort Knox. Here’s a breakdown of what you need to do:
- Treat CAs as Critical Assets
Your CA servers should be protected like domain controllers (or fort knox), lock them down and apply Tier 0 security controls. These systems are high-value targets, and attackers know it. - Audit and Harden Certificate Templates
Regularly audit your certificate templates and remove any unnecessary features, like SAN customization, which could give attackers an easy way in. Ensure templates are configured for minimum privilege. - Secure CA Private Keys
Store CA private keys in hardware security modules (HSMs). This keeps them away from prying hands and makes it significantly harder for attackers to steal them. - Monitor Certificate Activity
Keep an eye on your certificate enrolments, authentications, and template modifications. If something seems off, it probably is. Proactive monitoring can be your early warning system.
Conclusion
Active Directory Certificate Services isn’t inherently insecure, but its complexity makes it ripe for misconfiguration. When that happens, hackers can sneak in, steal credentials, and establish persistence that’s incredibly tough to detect and eliminate. As the Certified Pre-Owned whitepaper highlights, understanding the risks and securing AD CS is key to preventing these kinds of attacks.
To learn more about Secure usage & management of X509 Certificates, you can refer to this in depth Practitioners Guide authored by our founder Ajit Hatti as part of Null Cipher Security Club
In short, if you’re not securing AD CS, hackers might just settle in and stick around your network for longer than you’d like.
Read Also
Certified Pre-Owned: Abusing Active Directory Certificate Services
Microsoft Entra ID Vulnerabilities: Pass-Through Authentication Risks
Microsoft Reveals Russian Hack: Executives’ Emails Compromised

