Introduction
GitHub, a leading software development platform, faces a grave security threat posed by millions of malicious repository forks. Since mid-2023, attackers have exploited GitHub’s ecosystem, employing sophisticated tactics to infiltrate legitimate repositories and spread malware.
The Attack
The attack involves cloning existing repositories, injecting malware, and uploading them back to GitHub under the same names. Automated systems then fork these repositories thousands of times, amplifying the malicious spread. This campaign targets unsuspecting developers, executing code designed to steal sensitive information such as authentication cookies.
Timeline
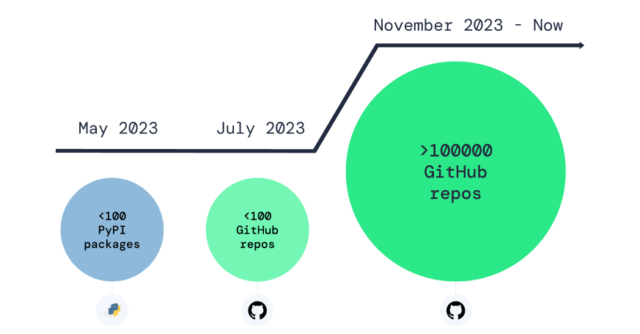
- May 2023: Malicious packages uploaded to PyPI, spread through ‘os.system(“pip install package”)’ calls in forks of popular GitHub repos.
- July-August 2023: Malicious repos uploaded to GitHub directly, bypassing PyPI after removal of malicious packages.
- November 2023-Now: Over 100,000 repos detected with similar malicious payloads, continuing to grow.
GitHub’s Response
GitHub employs automated tools to swiftly detect and remove malicious repositories. However, despite these efforts, some repositories evade detection, posing a persistent threat. GitHub encourages community reporting and has implemented default push protection to prevent accidental data leaks.
Implications
The widespread nature of the attack risks secondary social engineering effects, as naive users unknowingly propagate malware. GitHub’s security measures mitigate risks, but the incident underscores vulnerabilities in the software supply chain. Similar campaigns targeting dependencies highlight the fragility of software supply chain security.
How can PureID help?
Pure ID authentication framework provides enterprise users with individual commit-signing keys. All the changes to code repositories can be cryptographically verified at the build time, if it’s coming from a trusted user or not.
Without cryptographic verification its hard to determine if the code is committed from a trusted/original author and is free from any unauthorised commits or sanctity violation.
Removing passwords from authentication flow further hardens the security of the code repositories.
Conclusion
GitHub’s battle against malicious forks underscores the ongoing challenges in securing the software supply chain. Vigilance, community reporting, and enhanced security measures are essential to effectively mitigate risks in the ever-evolving threat landscape.
See Also: